Summary of Contents for Satel ETHM-2
- Page 1 Ethernet Module ETHM-2 Firmware version 2.00 ethm2_en 05/15 FreeRTOS is used in this product (www.freertos.org). SATEL sp. z o.o. ul. Budowlanych 66 80-298 Gdańsk POLAND tel. + 48 58 320 94 00 www.satel.pl...
- Page 2 SATEL's goal is to continually improve the quality of its products, which may result in alteration of their technical specifications and firmware. Current information on the introduced modifications is available on our website. Please visit us at: http://www.satel.eu...
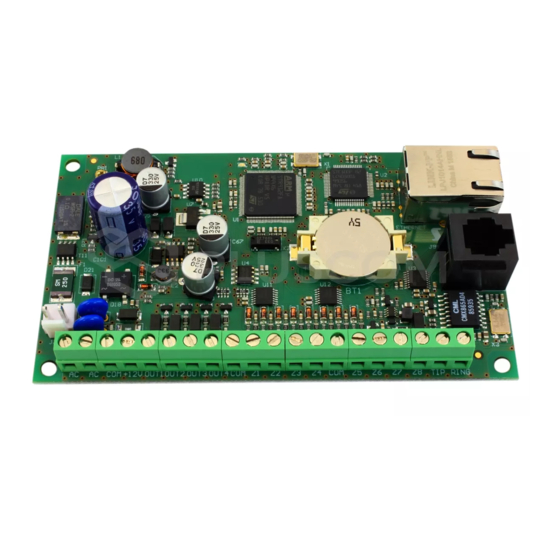
- Page 3 SATEL ETHM-2 The ETHM-2 Ethernet module is a dedicated device for use in intruder alarm systems for reporting purposes. It enables sending event codes via the Ethernet network (TCP/IP) to the STAM-2 monitoring station or SMET-256 converter. The module can interface with any alarm control panel (even if is not provided with telephone dialer).
- Page 4 5 – RS-232 port which enables the module to be connected to the computer serial COM port. The dedicated cable for making this connection, designated DB9F/RJ, is manufactured by SATEL. Using a computer with the ETHM-2 Soft program installed, you can configure the device and read the events.
-
Page 5: Installation
3. I NSTALLATION Disconnect power supply before making any electrical connections. The ETHM-2 module is designed for indoor installation, in spaces with normal humidity of air. The module can be supplied with alternating or direct voltage. 3.1 C ONNECTION OF ALTERNATING VOLTAGE If the module is to be supplied with 16 V AC (±10%), it is recommended that a 20 VA... - Page 6 ETHM-2 SATEL There are 2 available methods of the module configuration by means of the ETHM-2 Soft program: 1. Via Ethernet network. Data transmission in the network is encrypted by means of an advanced algorithm, based on 192-bit key. 2. Through the RS-232 port.
- Page 7 SATEL ETHM-2 5. Click on the symbol to initiate communication with the module. 6. The login window will be displayed. Enter in the fields: the user name (by default: “service” - see section L p. 6), OGGING DETAIL the password (by default: “service” - see section L p.
- Page 8 User – user name. Required during the procedure of logging into the module. The device can recognize two users: user with limited right of access to the device (only allowed to view the event log and control the inputs). Factory default: satel. user with full right of access. Factory default: service.
-
Page 9: Program Settings
JAVA port – enter in this field the number of TCP port which will be used for communication with the ETHM-2 Soft program via the Ethernet network. You can enter any value from 1 to 65535. The value must be different from that entered for the other ports. Default value: 33333. - Page 10 ETHM-2 SATEL TCP/IP – if this option is enabled, communication will be effected through the TCP/IP network. Address – IP address of the module with which communication is to be established. Port – number of the port through which communication with the module is to be effected.
- Page 11 SATEL ETHM-2 Fig. 6. Event codes in Contact ID format, “Reporting” tab. Monitoring station settings Server address – network address of the monitoring station. Port – enter in this field the number of TCP port through which communication with the monitoring station will be effected.
- Page 12 ETHM-2 SATEL or the entered telephone number is not consistent with that programmed in the control panel, the module will not be receiving events sent by the control panel. Extended kiss-off – some control panels require long acknowledgement of receiving the code in Contact ID format.
-
Page 13: "Inputs / Outputs " Tab
SATEL ETHM-2 Fig. 7. Event codes in SIA format, “Reporting” tab. 4.6.2 Test transmissions The “Test transmission” event can be generated: On time – every specified number of days at defined time. The first event will be generated at defined time on the same day when test transmission rules are saved to the module, or on the following day (if defined time on that particular day has already passed). - Page 14 ETHM-2 SATEL Bypass after – number of input violations which will result in bypassing the input. You can program values from 0 to 15. After entering 0, the input will not be bypassed. Bypass time – time during which the input will be bypassed after occurrence of the number of violations indicated in the “Bypass after”...
- Page 15 SATEL ETHM-2 Supply output overload E-mail message sending failures Note: The trouble signaling outputs cannot be controlled. 4.7.4 Control Inputs can control outputs by activating or deactivating them. Output operating time (after violation of the control input or after remote activation) should be programmed.
-
Page 16: "Event Log " Tab
- event code/e-mail message has been sent; • - event code/e-mail message is waiting to be sent; - sending the event code/e-mail message has been cancelled (ETHM-2 module user has disabled monitoring events/sending e-mails after the event occurred). 5. S PECIFICATIONS Nominal supply voltage: ............16 V AC ±10% or 12 V DC ±15%...

















Need help?
Do you have a question about the ETHM-2 and is the answer not in the manual?
Questions and answers